
We learn about unauthorized access from the beginning
The hacking was carried out by Apple’s Steve Jobs.
So he later became the CEO of the popular Apple company. But if we do something with someone’s computer, it’s just inside.
After all, trespassing is one of the most popular topics in the world today …
Like the title, this will teach you about hacking from the beginning .. but not how to do it! How hacking came into the world is about the then popular hackers.
From the last 40 years to various types of phones to websites Hacking attacks .. so there is nothing to say about it …
The word hacker first originated with students who studied and trained at MIT in the 1960s.
They are called phone hackers or freaks. The most famous and first person to do so was John Dropper. Otherwise known as Captain Crunch. In 1972, he modified a toy plastic tube and redesigned it to produce a 2600 Hz signal, allowing the phone’s subscriber to hear it, access the telephone network, and make free calls.

He later created a device called the blue box, which included different sound waves for each number. Information about the plan was soon published in Esquire magazine under the title “The Secret of the Little Blue Box”.

Since then, Apple’s CEO Steve Jobs and co – founder Steve Wozniak have further developed it, created the Blue Box in their own home and sold it for $ 150.
John Draper was arrested in 1976 and sentenced to four months in prison for damages to telephone companies.
With the development of computers in the 1980s, when computers became smaller, hackers began to focus on computers, using the BBS or bulletin board systems available at the time to exchange information and technology.
The most common of these were Sherwood Forest and Catch 22. Hacking groups also emerged. Among the first was the Legion of Doom in America
Chaos was at the forefront of the computer club in Germany.

With the release of War Games in 1983, he was able to show the world clearly what intrusion is. It was able to generate a great deal of interest and desire to produce hackers around the world.

The young man in the film tries to get into the computer of the player’s computer game.
What happens to him? See if he has time.
In the same year that the film was released, six youths were arrested for trespassing on 60 computers.
That group was known as the 414 gang.
In 1984, an unauthorized magazine called 2600 was launched, which was very popular at the time.
As computer crime increased, the US Congress enacted laws and regulations known as the CFAA (Computer Fraud and Abuse Act).
In 1988, Robert T. Schmidt, a student at Cronell University, the son of a leading U.S. defense agency scientist. Morris wrote software to test how the government’s ARPAnet network’s Unix email system works.
(Morris Worm) went down in history as a virus.

Within 12 hours of its installation, more than 60,000 computers in government institutions and universities were destroyed. Morris was expelled from university and fined $ 10,000 and sentenced to three years in prison.
He was the first person to be convicted under the Ceasefire Agreement. It is said that hackers still use his code.
The most infamous hacker case in the world was the arrest of three suspects at the Chaos computer club in Germany on suspicion of hacking into an American government computer system and leaking all of its operating system code to the Russian KGB intelligence service.
The current list of hackers is believed to have come from a hacker who was arrested in another incident the same year and identified himself as an advisor. That is
“My Crime us that of Curiosity…I am a hacker,and this is my manifesto.You may stop this individual, but you can’t stop us all.”
The Sun Devil operation, launched in 1990 by US intelligence to crack down on hackers, led to the arrest of many hackers for various offenses.
Receiving a Porsche 944S2 car and prize money for a 102 phone call from a popular KIIS Fm radio show in Los Angeles is one of the hallmarks of unauthorized entry into history. It has overcome this by making short calls themselves.

He was arrested in April 1991 and released in 1996. He is currently a freelance journalist reporting on computer crimes for Wired Magazine.
Kevin Mitnick, a computer hacker, was arrested in 1995 and sentenced to five years in prison for stealing more than 20,000 credit cards. He was the first computer hacker to be named an essential criminal by the US FBI.

He worked as a cleaner for a computer company in 1976, developing his skills at night using computers, how to connect a cell phone to a network, and how to steal Motorola’s data from Motorola, Nokia, Fujitsu, and Sun Microsystems. Has entered computer systems.
After his imprisonment, he was banned from using any electronic devices.
There is also an original book about him.
It’s called Ghost in the Wires.

Vladimir Levine has been arrested on charges of transferring more than $ 10 million from an American bank to his bank account worldwide from his work computer and fraudulently charging $ 400,000.
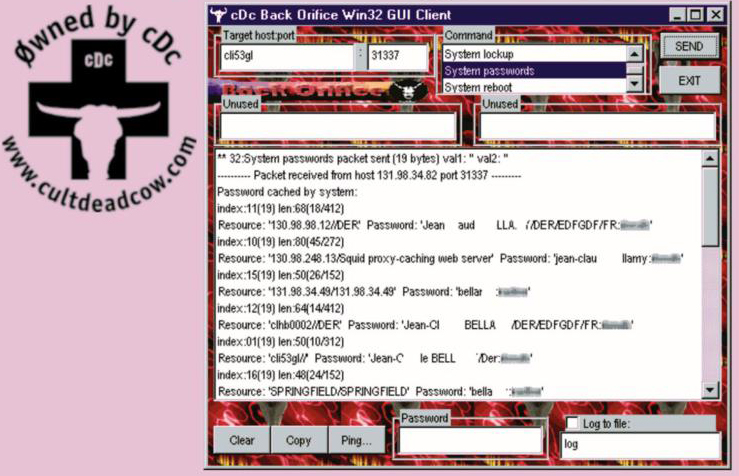
In 1998, a hacking group called Cult of the Dead Cow introduced a program called Back Orifice, which enabled Windows 95 and 98 operating systems from anywhere else.
During the Gulf War, software was hacked into the Pentagon’s computer system. At the end of the investigation, two 19-year-old American men were arrested.
Ehud Tenebom, who pretended to be an analyst, has been arrested and is currently working as a chief technology officer for a computer company.
Information about hackers in the past and hacking.
All of the above information and photos were taken from the Internet. Your comments
Be sure to post ..